Endpoint security has progressed. Endpoint security or endpoint protection is the cybersecurity approach to defending endpoints such as desktops laptops and mobile devices from malicious activity.

The Top 10 Privileged Access Management Pam Solutions 2022 Expert Insights
Endpoints are physical devices that connect to and exchange information with a computer network.
. If you find yourself selecting security products here are some of the common pitfalls many buyers make when evaluating them. The first major pitfall to avoid is not knowing what the market thinks. Some typical endpoint security solutions include traditional antivirus software endpoint.
What is NOT a commonly used endpoint security technique. Endpoint security is also the process of protecting the enterprise network via protecting the endpoint devices on the network from being infected with malware. Endpoint Security is a technique for preventing hostile actors and campaigns from obtaining access to endpoints or entry points on enduser devices including.
Endpoint protection is the ability to protect the assets that are the last touch point of the network it is connected to. Secure Manage Support Devices Anywhere with Dell Technologies Unified Workspace. Some examples of endpoints are mobile devices desktop computers virtual.
View the full infographic. Ad Modernize Deployment Security Management Support for Dell Trusted Devices with Intel. Endpoint security refers to the prevention detection and remediation of threats and cyberattacks that target any device connected to your network or cloud.
As the name suggests endpoint security is a term used to secure the endpoints and prevent any potential. What is NOT a commonly used endpoint security technique. Full device encryption Network firewall Remote wiping Application control What is NOT one of the three tenets of information.
The most common endpoint threats and attack techniques are. Endpoint security is an umbrella term that refers to security tools that protect end user devices. Beyond traditional endpoint detection and response tools enterprises have to upgrade to next-generation endpoint security solutions which use AI machine learning and.
Endpoint protection can also be called endpoint security.

Understanding The Importance Of Managed Network Services For Businesses

Ransomware Four Ways To Protect Data Now Security Solutions Data Solutions
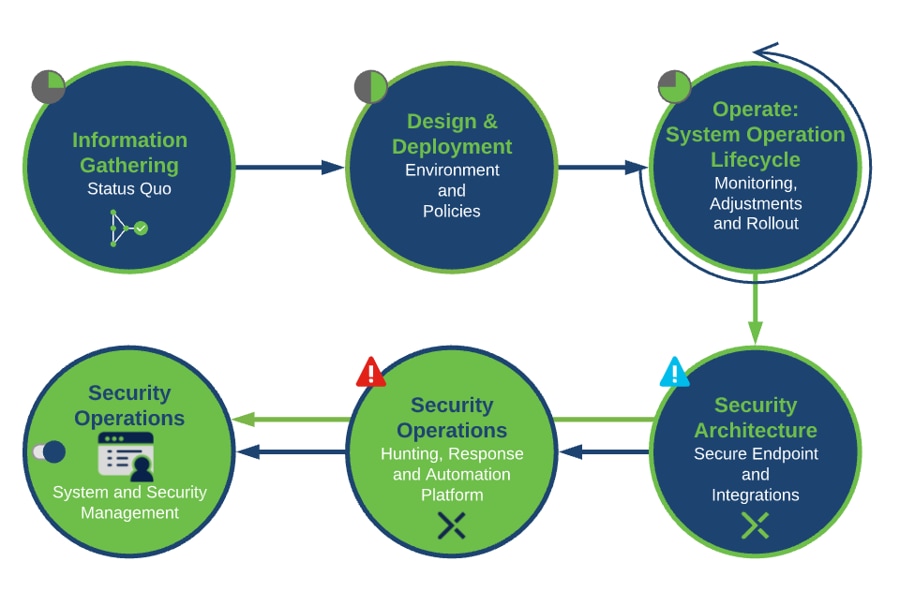
Secure Endpoint Best Practices Guide Cisco

Breastfeeding Infographic Breastfeeding Doula Www Douladarla Com Baby Breastfeeding Breastfeeding Breastfeeding Help

Fileless Attacks Surge In 2017 Security Solutions Are Not Stopping Them Security Solutions Security Cyber Security

Autottp Automated Tactics Techniques Procedures Regression Testing Multi Factor Authentication Life Cycles

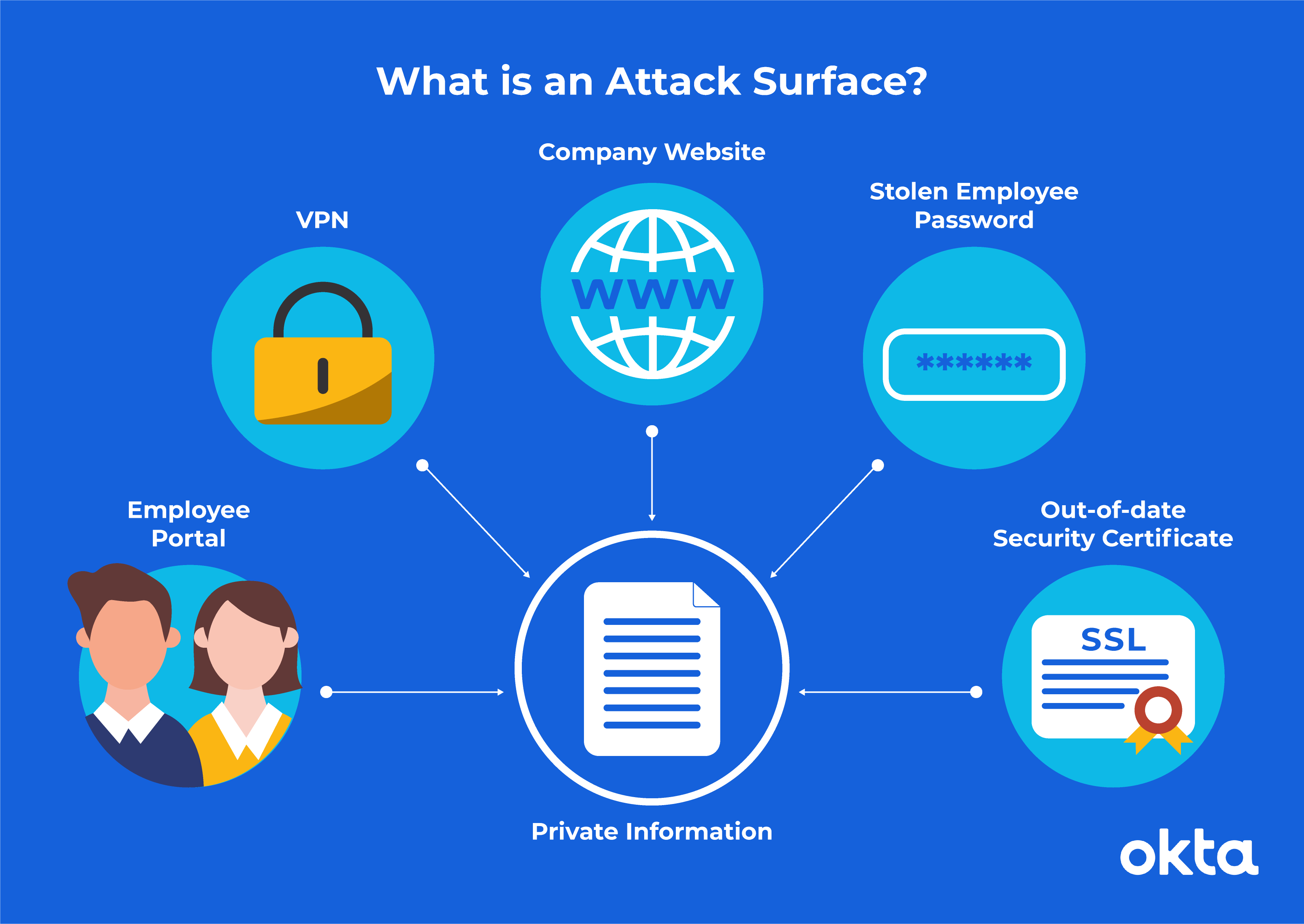
What Is An Attack Surface And How To Reduce It Okta

Free Image On Pixabay Security Department Safe System Cyber Security Security Solutions Cyber Security Certifications
0 comments
Post a Comment